VM Manager is a suite of tools that can be used to manage operating systems for large virtual machine (VM) fleets running Windows and Linux on Compute Engine.
VM Manager helps drive efficiency through automation and reduces the operational burden of maintaining these VM fleets.
VM Manager supports projects in VPC Service Controls service perimeters.
Overview
The following services are available as part of the VM Manager suite:
- Patch: Use this service to apply on-demand and scheduled patches. You can also use Patch for patch compliance reporting in your environment.
- OS inventory management: Use this service to collect and review operating system information.
- OS policies: Use this service to install, remove, and auto-update software packages.
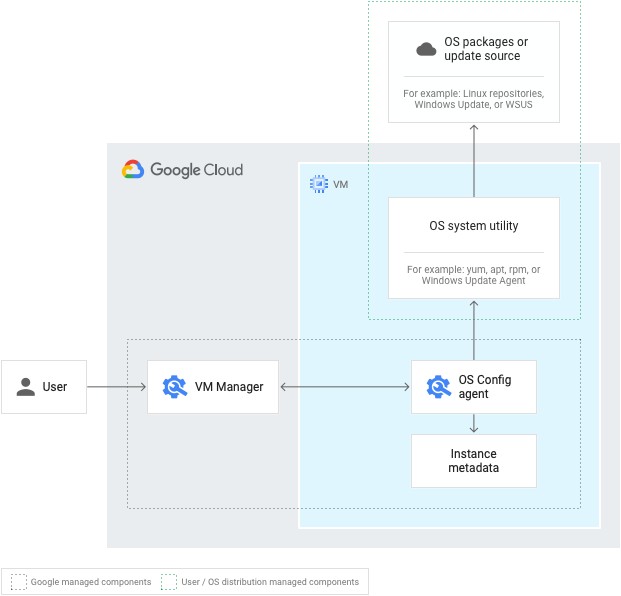
When you set up or enable VM Manager in your Google Cloud project, you can access the full suite of VM Manager tools: Patch, OS policies, and OS inventory management.
Enable VM Manager
You can set VM Manager to be automatically enabled or manually enabled. Automatic enablement applies to your entire project. Manual enablement can be done per VM or for the entire project.
In summary, when you enable VM Manager, whether automatically or manually, the following setup takes place:
- OS Config service API is enabled on the Google Cloud project.
The OS Config agent, running on each selected VM, is activated by setting the required instance metadata values.
For more information about manually enabling VM Manager, see Setup overview.
Automatic enablement is done from the Google Cloud console.
OS Config agent
When VM Manager is enabled, the OS Config agent functions as follows for each of the services:
- For Patch, the OS Config agent uses OS system utilities
(such as
yum,apt,rpmor the Windows Update Agent) to retrieve patches or updates from the OS package or update source and apply them to the VM. For more information, see How Patch works. - For OS policies, the OS Config agent uses OS system
utilities (such as
yum,apt,rpmor the Windows Update Agent) to maintain the state for the VM that is specified in the OS policy. For more information, see How OS policies work. - For OS inventory management, the OS Config agent collects inventory data. This inventory data is then stored in the instance metadata and in various log streams. This data can then be queried using the Google Cloud CLI. For more information, see How OS inventory management works.
Google Cloud OS Config Service Agent
Some Google Cloud services have Google-managed service accounts that allow services to access your resources. These service accounts are sometimes known as service agents. For more information about service agents, see Service agents.
VM Manager manages your VMs using a service agent that collects
information about your VMs on your behalf. The email for this Google-managed
service agent is
service-PROJECT_NUMBER@gcp-sa-osconfig.iam.gserviceaccount.com.
This account uses the Cloud OS Config Service Agent role (roles/osconfig.serviceAgent).
You can view your project's service agents and the roles granted to the service agents on the IAM page of the Google Cloud console. However, if you've revoked the Cloud OS Config Service Agent role for the service agent, you cannot view the service agent on the IAM page.
OS packages and update source
For both Patch and OS policies, your VMs must be able to access package sources and repositories. For VMs in private networks, you can set up Private Google Access.
VM Manager and Terraform
You can use Terraform to extend the scope of VM Manager to multiple projects in a Google Cloud organization. To learn how to create patch jobs and OS policy assignments by using Terraform and VM Manager, see the Terraform examples and tutorials in the OS Config GitHub repository.
For more information about Terraform configurations and its usage, review the documentation for the following resources:
For a list of available resources to get started with using Terraform, see Using Terraform with Google Cloud.
Pricing
For pricing information, see VM Manager pricing.
What's next?
- Learn about OS inventory management.
- Learn about Patch.
- Learn about OS policies.
